Migrating Maven Namespace to Central Portal
Step-by-step instructions how to migrate your Maven Namespace and update your CI
Step-by-step instructions how to migrate your Maven Namespace and update your CI

Open bookmarks in Firefox 50% faster using Microsoft PowerToys.
Helps you craft more effective instructions to improve matching accuracy in AI Auto Relation.
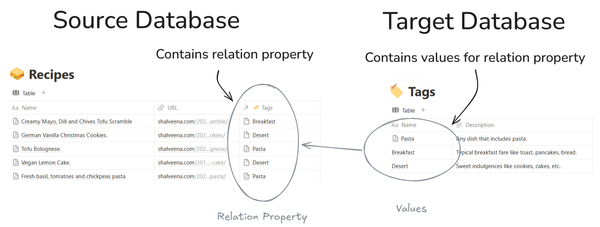
Provides guidance and examples for identifying which database relationships to automate in Notion.
30% of users did not successfully create an automated relation in Notion with my integration. Here I discuss the improvements I made to make it easier!
Describes two strategies for identifying why a particular page/database is not accessible by a Notion integration.
Explains all advanced configuration options available for AI Auto Relation for improving matching accuracy.
Detailed information for all four steps required to create a new AI Auto Relation in Notion.

11 sometimes surprising guidelines to find peace and make our mark on the world.

To steer or to float, that is the question.

It rains. The rain stops. The shrine gets cleaned.

Some random musings that, I hope, have some beauty in them.